September 18, 2023
The WG met again the week of September 4, 2023.
Here is the link to the meeting recording: https://youtu.be/rCRi57tdHns
TL;DR This table summarizes the status of the priority projects. The rows in blue seem to be the ones we can execute against right away:
| Project | Clear next step | Volunteers | ||
| Project Lead | User/Tester | Developer | ||
| Cloud Native / OCI runtime | Yes | Greg W | Yes | Yes |
| AD / DNS | Yes | Michael O | Yes | No |
| NVIDIA GPU | Yes | Greg W | Yes | No |
| Samba | Yes | Greg W | Yes | Yes |
| Definitive manager bhyve/VM/Jails | Yes | ? | Yes | No |
| Zero Trust Build | Yes | FreeBSD Foundation | Yes | No |
| Ports Automation | No | FreeBSD Foundation | Yes | No |
| Enterprise CA | Yes | Greg W | Yes | Yes |
Since this working group can likely make limited progress on Zero Trust Builds and Ports Automation, I suggest we move those into the parking lot and instead put Better certificate authority support in scope, as there seems to be a clear next step that can be addressed by the community.
We reviewed the results of the Feature and Infrastructure Priority and Difficulty survey, and began to plot next steps to work on the highest priority ones.
Here is how the WG ranked the priority of the feature and infrastructure needs for general purpose enterprise survey use cases.
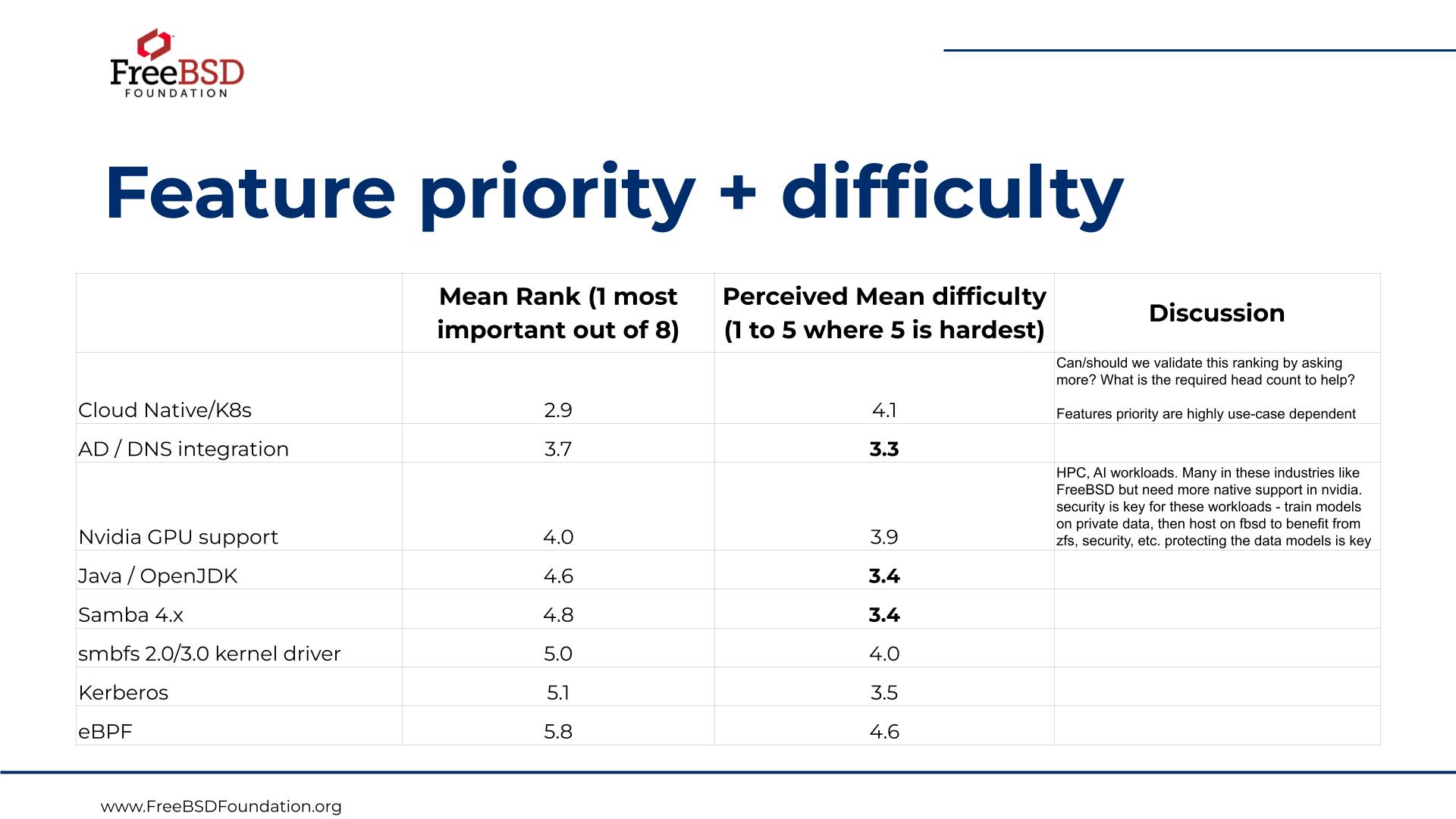
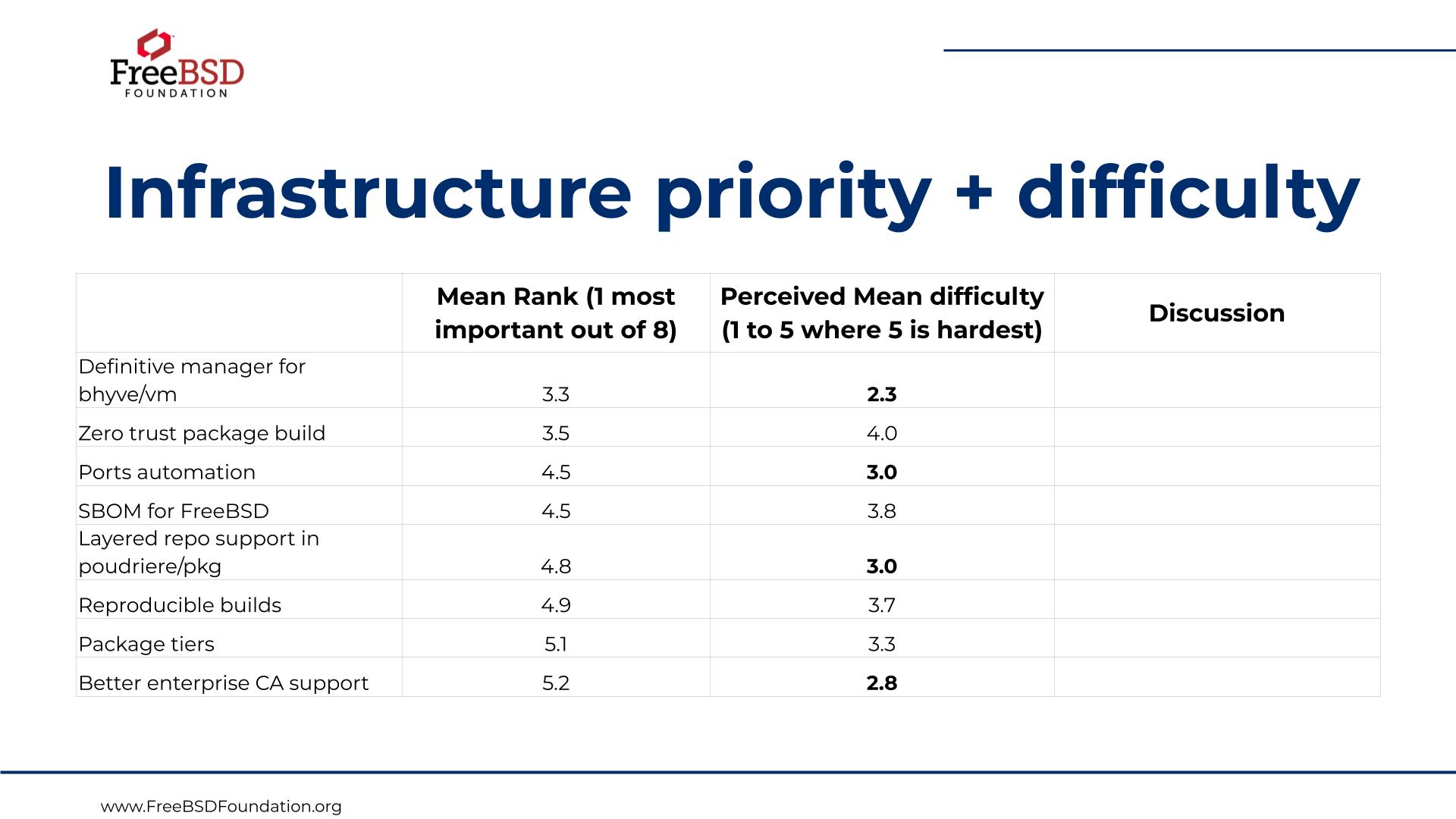
We then went through the top three in each category and discussed how to proceed.
Cloud Native / OCI runtime
This was considered the most important missing piece by a good margin. The great news is that there is existing work underway.
Here are the existing projects I am aware of:
| Name | Description | Link |
| Planternetes | port of K8s v1.28.0 to illumos and compiled the binaries for FreeBSD and OpenBSD | https://medium.com/@norlin.t/by-the-way-planternetes-kubernetes-v1-28-0-for-illumos-freebsd-and-openbsd-5d57026d6a25 |
| runj | a new experimental, proof-of-concept OCI-compatible runtime for FreeBSD jails. | https://samuel.karp.dev/blog/2021/03/runj-a-new-oci-runtime-for-freebsd-jails/ |
| ocijail | Experimental, proof-of-concept OCI-compatible runtime for jails | https://www.freshports.org/sysutils/ocijail/ |
| Podman port to FreeBSD | Use podman on FreeBSD to Manage Pods, Containers and Container Images | https://www.freshports.org/sysutils/podman/ |
| FreeBSD containers on macOS | Podman supports running Linux containers on popular client operating systems (macOS, Windows) so people can work on these systems and deploy into the cloud. It does this by spawning a Linux VM and connecting to it from the outside. This project aims to bring the same podman desktop/laptop experience that Linux server users enjoy to FreeBSD servers. | https://www.linkedin.com/pulse/freebsd-containers-macos-david-chisnall/ |
| XC | work-in-progress container engine for FreeBSD to run both Linux[1] and FreeBSD containers. It can support OCI compatible image registries[2] for image distribution, such as DockerHub, or Azure Container Registry. Notes from Talk at EuroBSDCon Running native and docker containers on FreeBSD, and distribute to OCI image registries Yan Ka Chiu | https://github.com/michael-yuji/xc |
| add basic FreeBSD support on Kubelet | first bricks to make kubelet start on FreeBSD and talk with CRI runtime (in my case, containerd+runj) to run (for now) FreeBSD containers. | https://github.com/kubernetes/kubernetes/pull/115870 |
Next steps
We agreed to the following next steps:
- Complete a very lightweight PRD so that we agree on the end result we are shooting for
- Need volunteers
- Develop test and documentation protocol and assess the above-listed approaches against the PRD
- Have 3 volunteer, need more
- Determine which approach(es) best fit the requirements and then determine how to get it/them to production-ready status
- Have 2 volunteers
- Have 2 volunteers
I have created a Wrike project with the above three tasks and will invite volunteers to join.
AD / DNS Integration
Looking for volunteers to help here. The next step is to have a call to scope out the existing state and what work is needed.
NVIDIA GPUs / CUDA
This one generated some great discussion. Support for these chips and drivers in FreeBSD is needed for HPC and AI workloads. Many users in these markets like FreeBSD for its security, stability, and performance but need more native support in nvidia. One usage model discussed would be to train models on private data, then host on FreeBSD to benefit from things like ZFS, security, etc. Protecting the data models is key, and hosting on FreeBSD is a great way to achieve this.
I offered to share the links to provide feature requests to Nvidia – here are two:
If the community can persistently request support on FreeBSD, hopefully we can get some assistance from NVIDIA.
Two others in the WG offered to help here. Thank you!
- Zoran, with Supermicro, can test and provide errors to help support the driver development
- Jason can help on Azure
I will have some opportunities next week to talk to some folks at NVIDIA and will bring up this discussion and report back on the response.
Samba
Earlier last week, we spoke with a developer with significant experience working with the Samba team. They will email the Samba team and offer to help get the patches upstream.
One of the things the Samba team, and other project, have asked for is GitHub Actions with FreeBSD to help automate things. The FreeBSD Foundation is going to connect with people at GutHub and Microsoft to try to get this in place.
I have created a Wrike project with the above three tasks and will invite volunteers to join.
Definitive manager for bhyve/VM/Jails
There are now 5-6 VM managers, mostly the same.
The WG seemed to agree that the best next step would be to organize a call or some sort of discussion with the maintainers of the various tools to see if there are efficiencies to be gained by consolidating.
Through this process, it would be desirable for there to be a default configuration.
Looking for volunteers to help here.
Enterprise CA (advanced this as it seems relatively low effort and b/c Zero Trust Builds and Ports Automation are not actionable by the WG right now)
Similar to AD/DNS, the next step here quick call – what’s open, what needs to be done, and we need someone who can get patches committed.
Greg to take action here to work with Joe/Ed/Others to figure out who is best person to help.
